Configure Validation
Overview
Monokle comes with sensible defaults. Out of the box it comes with YAML Syntax, Kubernetes schemas and it also checks the baseline profile of Kubernetes’ Pod Security Standards to prevent known privilege escalations.
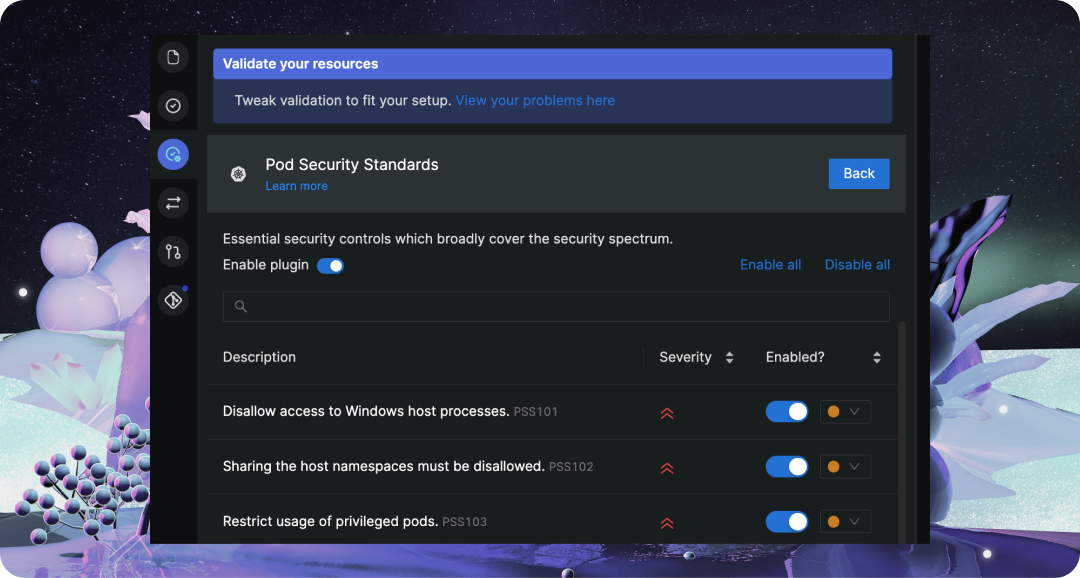
Configure validation by going to the validation activity in the IDE’s sidebar. The validator is modular and consists of plugins which each have a set of rules. You can configure each rule individually. You’ll need to make some decisions about which rules will be validated and what should happen when that rule fails.
Basics
Quickstart
Once you are ready to go beyond the defaults, you might not know which of the over 100 built-in rules to start with. You can go through the quickstart widget to conveniently setup presets based on standard security frameworks such as NSA Guidelines or different Pod Security Standards profiles. You can always revisit the quickstart to restore your configuration.
Rule Toggles, Severity & Level
Once you are ready to tweak the rules, get started by toggling a rule and see how your Kubernetes configuration will be revalidated in real-time.
The severity cannot be modified but instead acts as a helpful indicator whether rule violations might cause grave impact on your infrastructure. To learn more about the rule you can hover the description for additional details.
The level can be either a warning or error. Most often errors are prohibited and will be blocked on automated quality checks (e.g. during a step of your CI pipeline). Warnings are tolerated but should be improved over time. It is recommended to introduce a new rule as a warning to give the team some leeway to fix it.
Security Frameworks
Common frameworks like CIS Benchmarks or the Kubernetes Hardening Guidance of the NSA/CISA are defined as standard taxonomies. You can filter by them in the policy builder or the audit pane to quickly understand what you need to change to comply to these frameworks.
Plugin Settings
Occassionaly plugins have free-form settings. For example, the Kubernetes Schema plugin can be configured with your Kubernetes version to fetch more accurate schemas. Most often the UI will guide you to configure these settings. Alternatively you can use the (custom) plugin’s documentation in combination with the advanced YAML view described below.
Advanced
Configuration Format
Under the hood the validation configuration is actually a YAML file. This eases sharing configuration and interoperability between the tools in the Monokle ecosystem. You can also commit a monokle.validation.yaml to the root of your repository and we will detect that. Learn more about the format here.
# Example monokle.validation.yaml
plugins:
yaml-syntax: true
practices: true
kubernetes-schema: true
rules:
yaml-syntax/no-bad-alias: "warn"
yaml-syntax/no-bad-directive: false
practices/no-last-image: "err"
practices/cpu-limit: "err"
practices/memory-limit: "err"
settings:
kubernetes-schema:
schemaVersion: v1.24.2
The YAML View
The validation activity gives you a peek under the hood. This is handy for more advanced use cases such as (1) troubleshooting, (2) copy pasting configuration, or (3) configuring settings that are not available through the user interface.